Is your corporate email address connected to your LinkedIn account? If you answered yes, then you may want to consider changing that right now. Attackers have grown smarter over the years and are targeting these popular social platforms more than ever.
Since users are accustomed to getting email notifications from LinkedIn or other social platforms, it creates the perfect opportunity for cyber attackers to gain access to you. The example below is from a real phishing attempt that an attacker made against a LinkedIn user.
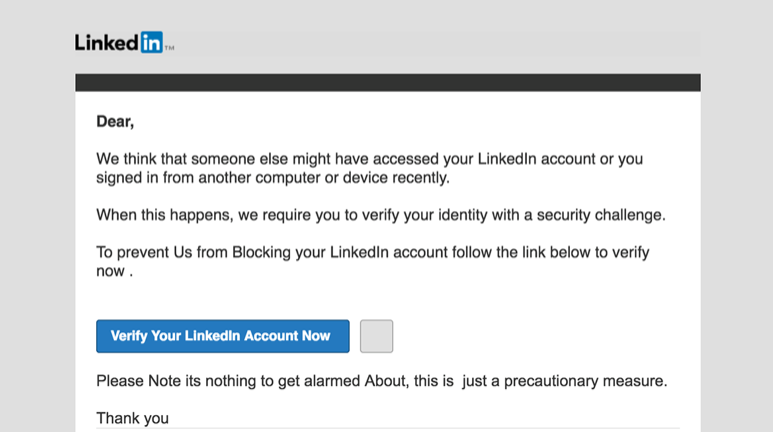
If you have received one of these messages, be wary. This goes for other emails that appear to be coming from LinkedIn too. “Someone viewed your profile” or “Someone wants to add you as a connection” are other notable subject lines that hackers have used. The best thing you can do is avoid clicking the link in the email and go straight to the source: your LinkedIn profile or app.
Attackers haven’t quite figured out the enigma code here. However, they do understand that your LinkedIn account may be connected to your corporate email address. Therefore, the attackers may be able to steal your LinkedIn credentials as well as your corporate email credentials.
Imagine this: You are at work on a corporate workstation and you receive a LinkedIn message alert to your corporate email. You click the link and it directs you to a page that looks exactly like LinkedIn. The message is from a job candidate and would like you to take a look at their resume. Seems innocuous enough, right? Wrong. You downloaded the attached PDF and you now have a piece of malware on your system that is undetected by your antivirus. The attackers may now have full control of your system.
Curiosity killed the cat—and your email security. Long ago, emails were used for legitimate business purposes. Then, the internet grew, and cyber-criminals went from lifting ATM machines to embedding file-less malware into cat videos. Our adversaries know that we are curious human beings and exploit this every single day.
Your LinkedIn and other social media accounts do not necessarily need to be connected to your corporate email address to present risks. Believe it or not, employees do access their personal email, social media, and other platforms at work. Yes, it is true, and it’s one of the high-risk activities that cybersecurity professionals are currently dealing with. Corporate policies go out the window in many instances and employees are operating platforms that put your business at heightened risk.
For example, an employee is on the corporate WiFi network from their smartphone. They receive a document from a colleague or friend via their personal email. However, they don’t know that the document is embedded with malware. Now, the attackers have control of the user’s smartphone and your corporate network.
Backdoors are everywhere in cybersecurity and these are some of the threats that are circumventing corporate policies, firewalls, antivirus, email spam filters, and more. Employees must be educated that the threats in the wild are not limited to their corporate email, firewalls, and local workstations. Attackers now have multiple avenues that can be leveraged to exploit organizations—including social media.
As ethical hackers and penetration testers, your employee’s LinkedIn accounts can give us invaluable information that can be used against them. By simply visiting a LinkedIn profile of a target, we can likely gather:
- Email Address
- Company Name
- Role
- Title
- Past Experience
- Charities
- Groups
- Interests
- Recent Posts
- Articles and Publications
- And more…
Using this basic information, attackers can send a phishing email to your corporate account that looks similar to this:
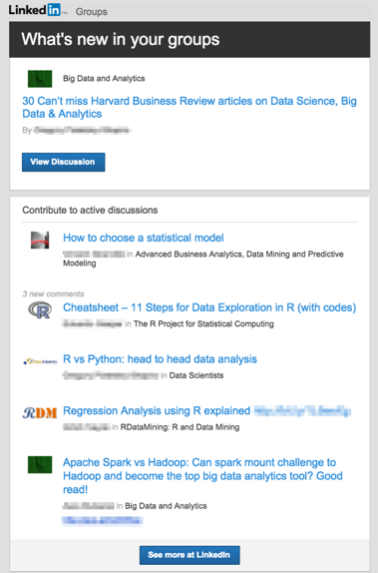
A personalized email like this establishes immediate trust because these are familiar items to you, which is why victims often succumb to such attacks.
Innocent victims are being exploited on a rolling basis and these types of attacks are rising, as detailed in a recent article by KnowBe4. Employees are innocent bystanders in this web of deception. However, even altruistic actions can lead to egregious consequences. Our corporate users must be trained and well-equipped with knowledge; as they are the first and last line of defense.

